As one who considers herself a spiritual person, as was raised as such, I'd like to think that I am fairly well-educated about most theological matters. I find it quite important to know what you believe and why. If nothing else, college has given me opportunity upon opportunity to "sharpen my claws," as it were. The same concept applies to computers. If you think that sounds cheesy, you may be right. After all, who would think that the belief you may base your values and morals on is akin to technological beliefs? Don't believe me? Try telling a Mac user that they may even be *remotely* wrong and you may have a technological Jihad on your hands. Personally, I don't mind debate, and even welcome it - so long as one is well-informed about their subject matter. What I believe that few people realize is that when they argue Mac vs. PC, they are essentially arguing over whether to have green beans or strawberries for dinner. They reach out to different target markets with little overlap.
The Church of Macintosh - I have to hand it to Apple. They know their market. Many of its consumers buy their products because they want a computer "they can just use." So, Apple heard the cries of their consumers and built one of the most stable OS's around - the Macintosh OS. You don't have to think to use it. That's the beauty of it. One of the primary factors leading to its stability is the proprietary hardware, Apple's middle finger stuck out to you daring you to not try to install its OS on any other hardware. (Hackintosh to the rescue!) I see that anyone who tries to use it beyond its capability (which isn't saying much) happens to be the one to experience problems with it.
Then we have the all-inclusive Apple Care. If you were able to actually afford the machines in the first place, you have to pay more for the AppleCare - the only way you're going to get the computer fixed for cheap, if not free. Now, I have heard no complaints about AppleCare. In fact, I hear nothing but praises from them. Still, one would think that after paying the nearly 50% premium for a Mac, they would just get the AppleCare with the product.
The other reason people love the Mac so much is that it doesn't get viruses. A quick read of this FierceCIO article and a US-Cert site search will tell you otherwise. The only reason they don't get many viruses now is because of their low market share. While their individual market share is increasing, their corporate share is lost to Microsoft. Corporations are who hackers generally want to go after.
The Microsoft Cathedral - While Apple is busy reaching out to the average everyday tech consumer, Microsoft is focusing on one of its strengths - business software. Their Azure program was released primarily for businesses (if you want a private cloud, just get a VM). After being at the TechEd Conference and through the Imagine Cup IT Challenge competition, I have found that it is possible to run your entire home, business and IT architecture off of Microsoft products alone. I'd like to see any other proprietary-based software company do that. This is why Microsoft has a majority of the corporate market share.
One of the things that I believe Microsoft suffers from is the same as Google with their Android phones - hardware inconsistency. If you want to build a computer from scratch, you build a Windows computer. Within reason, you can customize it right down to the amount of circuits you want on your motherboard, and if your mobo was properly built, Windows will still run on it. Fantastic and terrible at the same time. The only real trouble with such hardware flexibility is that with inconsistent specifications, you're going to get inconsistent software behavior. All an OS is is a GUI interface between the user and the hardware. So, it is up to Microsoft to continue broadening their OS's capability to communicate with different types of hardware.
Amazingly enough, Microsoft only now started including anti-virus software with its Windows 7 machines (not that it didn't need it).
While Apple is indeed catching up in the gaming department, so far, nothing's been able to beat Windows Aero in the graphics viewing - a gamer's dream come true! =)
Linux - What? No church name? Linux does not need that purely because there is no standard to measure against. What I mean by that is that if I tried to compare the Linux OS, then I would have to compare all distributions - maybe that'll be another post. These OS's are more for the saavy who just likes to make their own things - which I admire. I like the spirit of the developers. Heck, I've been contemplating turning this laptop into a Linux box. We'll see about that though.
Tl;dr - Don't bother with Linux unless you a) *really* don't want to think about what you're clicking (might I suggest Ubuntu or Mandriva?) or b) can do nothing *but* think about what you're doing (you'd love back-trac, RedHat, Fedora, etc).
In the end, it's all a matter of personal taste and needs. A Mac is going to be better at fulfilling some needs more than Microsoft is and vice-versa.
The Church of Macintosh - I have to hand it to Apple. They know their market. Many of its consumers buy their products because they want a computer "they can just use." So, Apple heard the cries of their consumers and built one of the most stable OS's around - the Macintosh OS. You don't have to think to use it. That's the beauty of it. One of the primary factors leading to its stability is the proprietary hardware, Apple's middle finger stuck out to you daring you to not try to install its OS on any other hardware. (Hackintosh to the rescue!) I see that anyone who tries to use it beyond its capability (which isn't saying much) happens to be the one to experience problems with it.
Then we have the all-inclusive Apple Care. If you were able to actually afford the machines in the first place, you have to pay more for the AppleCare - the only way you're going to get the computer fixed for cheap, if not free. Now, I have heard no complaints about AppleCare. In fact, I hear nothing but praises from them. Still, one would think that after paying the nearly 50% premium for a Mac, they would just get the AppleCare with the product.
The other reason people love the Mac so much is that it doesn't get viruses. A quick read of this FierceCIO article and a US-Cert site search will tell you otherwise. The only reason they don't get many viruses now is because of their low market share. While their individual market share is increasing, their corporate share is lost to Microsoft. Corporations are who hackers generally want to go after.
The Microsoft Cathedral - While Apple is busy reaching out to the average everyday tech consumer, Microsoft is focusing on one of its strengths - business software. Their Azure program was released primarily for businesses (if you want a private cloud, just get a VM). After being at the TechEd Conference and through the Imagine Cup IT Challenge competition, I have found that it is possible to run your entire home, business and IT architecture off of Microsoft products alone. I'd like to see any other proprietary-based software company do that. This is why Microsoft has a majority of the corporate market share.
One of the things that I believe Microsoft suffers from is the same as Google with their Android phones - hardware inconsistency. If you want to build a computer from scratch, you build a Windows computer. Within reason, you can customize it right down to the amount of circuits you want on your motherboard, and if your mobo was properly built, Windows will still run on it. Fantastic and terrible at the same time. The only real trouble with such hardware flexibility is that with inconsistent specifications, you're going to get inconsistent software behavior. All an OS is is a GUI interface between the user and the hardware. So, it is up to Microsoft to continue broadening their OS's capability to communicate with different types of hardware.
Amazingly enough, Microsoft only now started including anti-virus software with its Windows 7 machines (not that it didn't need it).
While Apple is indeed catching up in the gaming department, so far, nothing's been able to beat Windows Aero in the graphics viewing - a gamer's dream come true! =)
Linux - What? No church name? Linux does not need that purely because there is no standard to measure against. What I mean by that is that if I tried to compare the Linux OS, then I would have to compare all distributions - maybe that'll be another post. These OS's are more for the saavy who just likes to make their own things - which I admire. I like the spirit of the developers. Heck, I've been contemplating turning this laptop into a Linux box. We'll see about that though.
Tl;dr - Don't bother with Linux unless you a) *really* don't want to think about what you're clicking (might I suggest Ubuntu or Mandriva?) or b) can do nothing *but* think about what you're doing (you'd love back-trac, RedHat, Fedora, etc).
In the end, it's all a matter of personal taste and needs. A Mac is going to be better at fulfilling some needs more than Microsoft is and vice-versa.
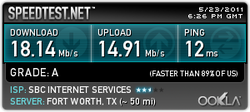
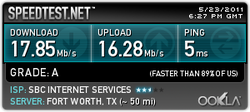
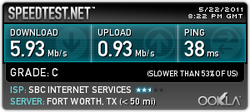
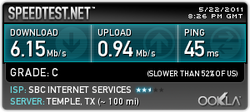
 RSS Feed
RSS Feed
