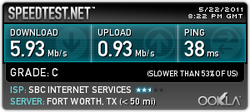
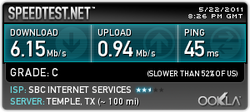
Due to some needed correction, I have redone the test and made sure that they both came from the same servers (thanks, Billy!).
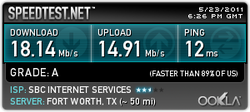
Google Chrome
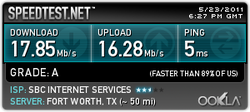
IE9
Eh...they have their trade-offs, it looks like.
My guess would be that given that we were on a Microsoft network in Atlanta, that something was configured specifically for the browser, IE9. Still, "kudos" to Microsoft for making their browser a great deal better over time.
I still maintain that Bing makes for an awful verb.
Professional Tip of the Day: Now go Bing yourself.
Eh...they have their trade-offs, it looks like.
My guess would be that given that we were on a Microsoft network in Atlanta, that something was configured specifically for the browser, IE9. Still, "kudos" to Microsoft for making their browser a great deal better over time.
I still maintain that Bing makes for an awful verb.
Professional Tip of the Day: Now go Bing yourself.
 RSS Feed
RSS Feed
