I know so many open source and Mac fanboys who will be angry with me after this...
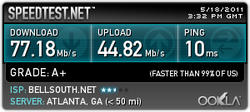
The SpeedTest results from Google Chrome.
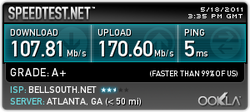
The SpeedTest results from Internet Explorer 9.
I actually tried both of these browsers in the speed test several times, but to no avail. While specific results varied, the winner was clear. What's interesting is that they both perform quite abismally (compared to what this network is capable of giving out) when they are both open. Chrome and IE do not get along (understandably). I am not entirely sure how the processes in IE work, but I do know that in Chrome, there is a separate process open for every tab. This may slow things down a bit.
However, all of this is rather moot considering the guy next to me gets > 400 mbps. It sounds like I need to figure out some network connection configurations. I think I'll Goog...uh, Bing that.
To make you open source and Mac fanboys happy, I will do the same test when I get back home to Texas. I am willing to accept that something got rigged (though I doubt it).
-Angela Fox
P.S. I really like Microsoft in general (anyone who knows me knows this), but it sounds really wrong to "Bing" someone. <*gasp!* I did NO such thing!!>
I actually tried both of these browsers in the speed test several times, but to no avail. While specific results varied, the winner was clear. What's interesting is that they both perform quite abismally (compared to what this network is capable of giving out) when they are both open. Chrome and IE do not get along (understandably). I am not entirely sure how the processes in IE work, but I do know that in Chrome, there is a separate process open for every tab. This may slow things down a bit.
However, all of this is rather moot considering the guy next to me gets > 400 mbps. It sounds like I need to figure out some network connection configurations. I think I'll Goog...uh, Bing that.
To make you open source and Mac fanboys happy, I will do the same test when I get back home to Texas. I am willing to accept that something got rigged (though I doubt it).
-Angela Fox
P.S. I really like Microsoft in general (anyone who knows me knows this), but it sounds really wrong to "Bing" someone. <*gasp!* I did NO such thing!!>
 RSS Feed
RSS Feed
